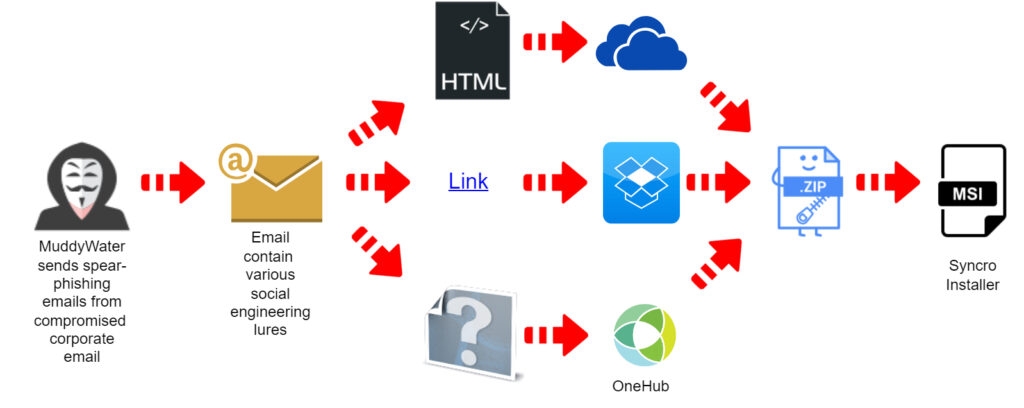
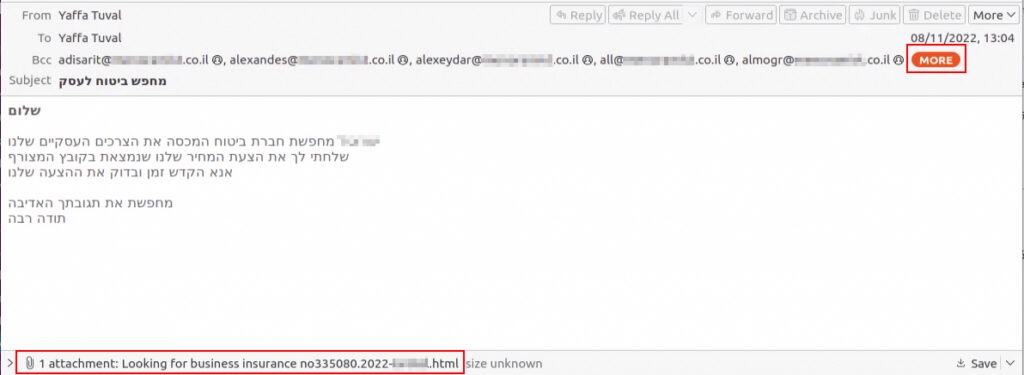
As per Deep instincts, the Muddy water group has applied this new tactic in the campaign, which might have started in September but only got noticed in October and also with the use of authentic remote administration software. Well, the researchers at Deep Instincts mention that Muddy Water has also used the remote administration tool in their earlier campaigns from 2020 to 2021, which were dependent on Remote Utilities and ScreenConnect. In a different campaign used the same tactics but switched to Atera Agent! (It is simply a system to monitor computers and servers that you wish to monitor) was discovered by Simon Kenin (A researcher at Deep Instincts). In Addition to this, the researchers at the security firm also discovered a new campaign in October by Muddy Water in which the group used Syncro (It is software for managed service providers). Simon Kenin in a report noted that the initial phishing emails were indeed sent from legitimate corporate email accounts that were compromised by the hackers. The researcher further added that the company signatures were not present on the phishing emails that the hacker group sent. However, the target still trusted the email as a legitimate email as it came from an authentic address belonging to the company they know. Well, among other targets of the hacker group, there were two Egyptian hosting companies. One of them was breached and used for sending phishing emails, and the other one received a malicious email. This is one of the known methods to gain trust since the receiver knows the company. To minimize the risk of getting detected by the security software/tools, the hacker group attached an HTML file that had a link to download the Syncro MSI Installer. Furthermore, the attachment is not an archive or an executable which does not make the user suspicious as HTML is mostly overlooked in phishing training and simulations, added Deep Instincts. Read: Threat Actor Targets Telecom Service Providers and Alters Defensive Methods When Detected The service was hosted on Microsoft OneDrive file storage, and the previous email was sent from the compromised email account of the Egyptian hosting company & Syncro installer was stored in Dropbox. Although according to Kenin, most of the Syncro installers that the hacker group used were hosted on OneHub’s Drive cloud storage which has been used in previous hacking campaigns. One thing to note here is that Syncro Installer has also been used by threat attackers such as LunaMoth. Moreover, the Syncro installer comes with a 21-day trial which has the full web interface and provides complete control over the computer which has the Syncro agent installed on it. Well, once the Syncro agent is on the target/victim’s computer, the threat attackers can use it to dispose backdoor and begin persistence and steal data as well. Some of the other targets of the Muddy Water group in this campaign include multiple insurance companies in Israel and the threat actors used the same tactics, i.e., hacking an email account of the company of the Israeli hospitality industry and then sending phishing emails from the hacked email account. To make it look like insurance, the hacker group added the HTML attachment link to the Syncro installer hosted on OneDrive. The phishing email was written in Hebrew (the national language of Israel). With that being said, Muddy waters methods are not modern. Yet the freely available software/tools can be an effective way for hacking practices. The threat actors use different names such as Static Kiten, Cobalt Ulster, and Mercury. It has been active since 2017. Read: What to Do When You Lose Internet: Basic Internet Connection Troubleshooting